Linux
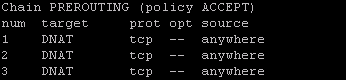
First of all I list all the rules including line numbers like this; iptables -L -t nat –line-numbers I then look at the output that will be similar to the below In this example lets say I want to delete rule number 2 in the PREROUTING chain, […]
Using yum to manage installing, upgrading or removing packages in Linux is a great little tool. Sometimes when running a yum transaction you may get a warning that you need to run “yum-complete-transaction” as you have pending or incomplete transactions. Simply running yum-complete-transaction will not do the trick if you […]
Sometimes I have the need to send an email with an attachment directly from the console, to do this I use a small email client called “mutt” it can be installed in Centos using;
I often am faced with deleteing mails from MAILER-DAEMON that are going to non existant domains in my Postfix queue. Rather than manually deleting each email by hand, I now use a little script that does the job for me. All I do now is type in “delmd” without the […]
I have just been working on a site that needs PHP 5.2 or above. The stock repositories for Centos that are provided by Virtualmin do not contain the PHP version I needed. However they do provide a Bleeding Edge packages, these must only be used if you know what you are […]
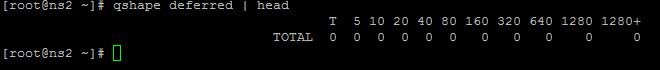
To check how many emails have been queuing in Postfix (an email server for Linux) and for what period of time you can use the following command #qshape deferred | head The above command will produce the following; The T represents time in minutes The Total represents how many emails have […]
If you have a MySql database that you want to import (pipe) into another server, as long as you have the filename.sql file you can copy it using WinSCP from the old server to the new server and run the following command;
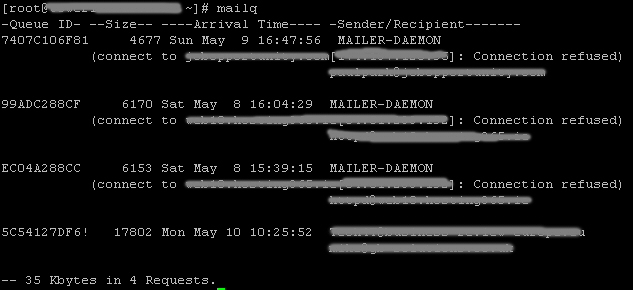
The below is what I do to delete an email from a Postfix queue. First we need to locate the email that you want to delete from the postfix queue mailq
On your VM host you need to initiate installing the VMware tools into your guest. Once this has been done the remaining steps are carried out on the guest OS. As root you need to mount the VMware Tools virtual CD-Rom image#mount /dev/cdrom /mnt
Custom rules can be created for Spamassassin, I use a hand written list thats customised for my needs. The location of the file is /etc/mail/spamassassin/98_myrules.cf The file name is not important, the format of the file is as follows:- body LocalStockRule /putcompanynamehere/ describe LocalStockRule Local Stock Name Block score LocalStockRule […]
Linpus on an Acer Aspire One netbook, does not ship with an SSH client. To be fair its not probably needed by the average user. When I use my wifes AA1 to check my linux mail servers (postfix). I found that I could not SSH so had to install it […]
Copy folder using command line This is an example how to copy a folder using the command line. i.e I want to copy the folder ‘Aqua’ on my desktop to /usr/share/amsn/skins. What is the command using the terminal? sudo cp -R ~/Desktop/Aqua /usr/share/amsn/skins/ Sudo is because you need root privileges […]
OK, we live in the wonderful world of Linux. BUT, for many of us, having to deal with Windows is a fact of life. For example, you may want to use a Linux server to back up Windows files. This can be made easy by mounting Windows shares on the […]
The virtual machines default store is located in;- \var\lib\vmware\Virtual Machines This is for Centos. The position of the default store on Windows is;- c:\Virtual Machines