What have Google done? on browsing to www.google.co.uk I was shocked to see that Google known and loved for its no nonsense, fast loading search page are now trying to look like Microsoft’s search engine – Bing. Google get back to your roots and don’t be a sheep following Microsoft! […]
Technical
Apple iPad’s UK launch date and pricing finally revealed Apple fans will need to dig deep… Follow the link for more details http://nl.silicon.com/s/8514t/6b603779711020
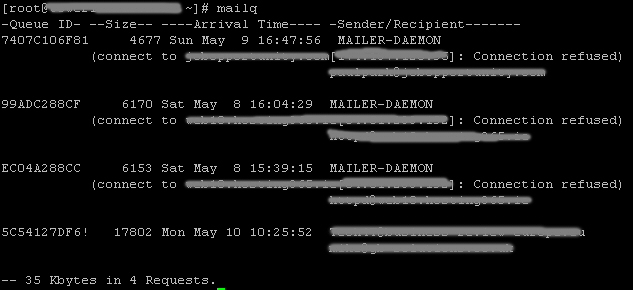
The below is what I do to delete an email from a Postfix queue. First we need to locate the email that you want to delete from the postfix queue mailq
On your VM host you need to initiate installing the VMware tools into your guest. Once this has been done the remaining steps are carried out on the guest OS. As root you need to mount the VMware Tools virtual CD-Rom image#mount /dev/cdrom /mnt
Here I am going to explain how to stop and start VM’s that are ruuning under ESXi 4.0 server, first you have to enable SSH on the server. Once you have enabled SSH, connect to the ESXi server using putty or your prefered SSH client.
If you are unable to connect to ADSL using the login details provided by your ISP, then try the alternatives below to test your connection. Here are the login settings to use for your router or modem to connect to the BT test domain. User: bt_test@startup_domain BT will ignore any […]
What you are trying to accomplish here is to have one resource (either a page or an entire site) redirect a visitor to a completely different page or site, and while doing so tell the visitor’s browser that the redirect is either permanent (301) or temporary (302). Microsoft’s Internet Information […]
Custom rules can be created for Spamassassin, I use a hand written list thats customised for my needs. The location of the file is /etc/mail/spamassassin/98_myrules.cf The file name is not important, the format of the file is as follows:- body LocalStockRule /putcompanynamehere/ describe LocalStockRule Local Stock Name Block score LocalStockRule […]
Linpus on an Acer Aspire One netbook, does not ship with an SSH client. To be fair its not probably needed by the average user. When I use my wifes AA1 to check my linux mail servers (postfix). I found that I could not SSH so had to install it […]
Copy folder using command line This is an example how to copy a folder using the command line. i.e I want to copy the folder ‘Aqua’ on my desktop to /usr/share/amsn/skins. What is the command using the terminal? sudo cp -R ~/Desktop/Aqua /usr/share/amsn/skins/ Sudo is because you need root privileges […]
OK, we live in the wonderful world of Linux. BUT, for many of us, having to deal with Windows is a fact of life. For example, you may want to use a Linux server to back up Windows files. This can be made easy by mounting Windows shares on the […]
To change the DHCP lease period for a Zyxel P-660R-D1 router, telnet into the router and at the command line type “ip dhcp enif0 server lease 120” This will set the DHCP lease tim to 120 seconds. If you wanted to have the lease time set to 1 hour you […]
The virtual machines default store is located in;- \var\lib\vmware\Virtual Machines This is for Centos. The position of the default store on Windows is;- c:\Virtual Machines
The below will show you how to add the Dag Wieers repository to Centos 5.3 I have also used this method for lower versions of Centos as well. First you need to run this code from the console or via putty. rpm –import http://dag.wieers.com/rpm/packages/RPM-GPG-KEY.dag.txt In order to add this repository […]
Requirements: You have to have direct access to console 1.) While you are at the console hit ALT + F1 2.) Type in ” unsupported ” and hit Enter 3.) Go ahead and type the root password 4.) Go and edit the /etc/inetd.conf file type : vi /etc/inetd.conf 5.) Uncoment […]